What is Subdomain Takeover?
Subdomain takeover is a security threat that arises when an organization neglects to maintain or properly terminate the use of a subdomain associated with their main domain. This oversight could result from services hosted on external platforms (like AWS, Heroku, Azure, etc.) that, when not properly configured or decommissioned, can leave subdomains vulnerable.
Source HackerOne: https://www.hackerone.com/application-security/guide-subdomain-takeovers
Risks Associated with Subdomain Takeover:
- Domain Spoofing and Phishing: Malicious actors can take over abandoned subdomains to create fake websites that mimic the organization’s legitimate services, leading to phishing attacks on unsuspecting users.
- Man-in-the-Middle Attacks: Attackers could intercept communications by redirecting traffic from the compromised subdomain, enabling them to steal sensitive information or perform other malicious activities.
- Brand Reputation Damage: Subdomain takeover incidents can tarnish an organization’s reputation if attackers misuse the compromised subdomain for illegitimate purposes.
Common Causes of Subdomain Takeover:
- Unused Subdomains: Organizations often forget to remove DNS records or terminate services associated with subdomains that are no longer in use.
- Improper Configuration: Misconfigured DNS settings or incomplete cleanup after ceasing the use of external services can lead to subdomain vulnerabilities.
Preventive Measures:
- Regular Audits: Conduct periodic reviews to identify and remove unused or redundant subdomains from DNS records.
- DNS Monitoring: Employ tools that monitor DNS configurations to detect changes or anomalies in subdomains.
- Proper Termination Protocols: Ensure proper termination procedures are followed when discontinuing services associated with subdomains on third-party platforms.
- CSP (Content Security Policy): Implement robust security policies to prevent unauthorized domain access or embedding content from vulnerable subdomains.
- Subdomain Takeover Testing: Periodically conduct security assessments or penetration tests to identify potential subdomain takeover vulnerabilities.
Remediation Steps for Identified Vulnerabilities:
- Notify Service Providers: If vulnerabilities are detected on external platforms, notify the service providers to rectify misconfigurations or terminate services properly.
- Remove DNS Records: Immediately remove DNS records pointing to abandoned or unused subdomains.
- Revoke Access Tokens and Keys: Invalidate any API keys, access tokens, or credentials associated with the compromised subdomains.
Conclusion:
Subdomain takeover poses a serious threat to organizational security, potentially leading to various cyber attacks and reputational damage. Implementing proactive measures, conducting regular audits, and promptly addressing identified vulnerabilities are crucial steps in preventing subdomain takeover incidents.
By staying vigilant, maintaining robust security practices, and ensuring proper management of subdomains, organizations can mitigate the risks associated with subdomain takeovers, safeguard their online assets, and uphold their reputation in the digital landscape.
Stay Secure! 🔒✨
Remember, keeping up-to-date with the latest security practices and promptly addressing vulnerabilities is essential in mitigating risks associated with subdomain takeover.
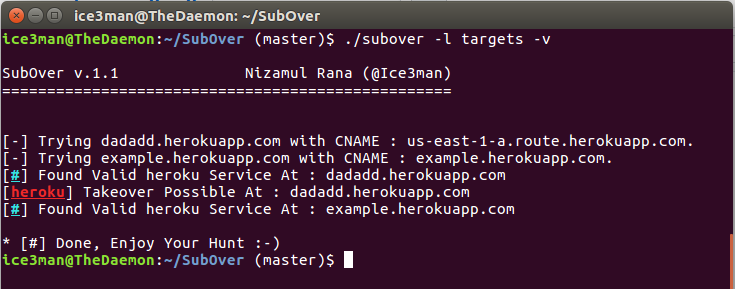
Some great tools for subdomain takeover :
Enum subdomain:
https://github.com/aboul3la/Sublist3r
https://github.com/projectdiscovery/subfinder
Scan Subdomains list :
https://github.com/Ice3man543/SubOver